[ad_1]
Researchers spoofed over 1,700 applications from 120 publishers and stopped a “massive” ad fraud scheme that affected nearly 11 million devices.
“VASTFLUX is a malvertising attack that injects malicious JavaScript code into digital ad creatives, allowing fraudsters to stack numerous invisible video ad players on top of each other to register ad views.” said fraud prevention company HUMAN.
The name of this operation comes from the use of DNS evasion techniques called Fast Flux and VAST (digital video ad serving templates used to serve ads to video players).
This sleight of hand specifically exploited the restricted in-app environment that runs ads on iOS to bid to display ad banners. If it wins the auction, it uses a hijacked ad slot to inject malicious JavaScript and establish a connection with a remote server to retrieve the list of targeted apps.
contains bundle identities belonging to legitimate apps and performs what are known as app spoofing attacks. In this attack, a rogue app masquerades as a highly rated app in an attempt to trick advertisers into bidding on ad space.
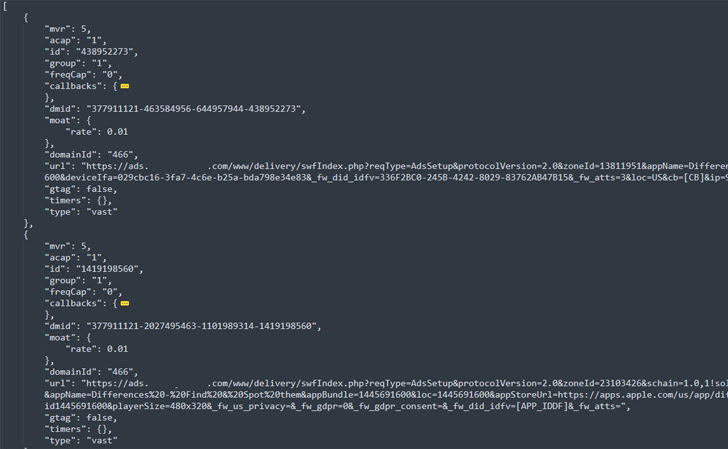
According to HUMAN, the ultimate goal was to register views of up to 25 video ads by layering them in a way that was completely invisible to users and generated illegal revenue.
“But it’s more than just stacked ads,” the company said. “Many of the ads that may be displayed on a user’s device at once continue to load new ads until the ad slot containing the malicious ad code is closed.”
“The attackers behind the VASTFLUX scheme are clearly familiar with the digital advertising ecosystem,” he adds, adding that the campaign uses an endless stream of ads to trick both the advertising companies and the apps displaying the ads. It states that it also rendered a “playlist”.
The removal of VASTFLUX arrives three months after the suspension of Scylla, a scam targeting advertising software development kits (SDKs) within 80 Android apps and 9 iOS apps exposed on official storefronts .
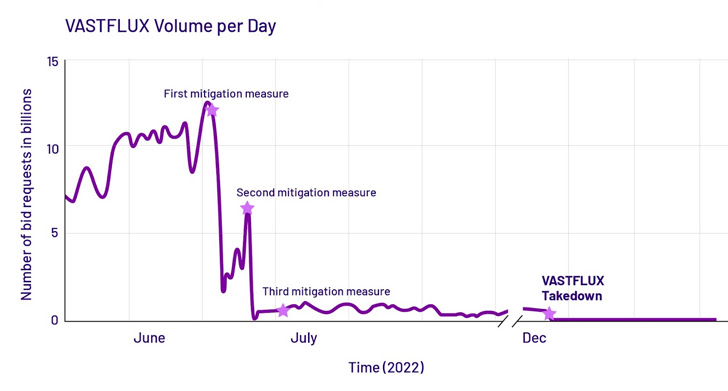
VASTFLUX, which generated over 12 billion bid requests per day at its peak, is just the latest in a string of recently shut down ad fraud botnets, joining 3ve, PARETO and Methbot.
[ad_2]
Source link