[ad_1]
The United States and other financial and law enforcement agencies are stepping up efforts to sanction crypto entities. The United States and its Office of Foreign Assets Control (OFAC) have changed the modus operandi employed to impose sanctions.
The results of this different approach have been mixed, and for many in the cryptocurrency industry they have set a new paradigm and crossed a line that had been respected by US institutions in the past. Most notable were the sanctions against the Ethereum-based decentralized exchange Tornado Cash and its developers.
Number of cryptocurrency sanctions on the rise in 2022
US law enforcement used to impose sanctions on individuals and entities, according to a report from on-chain analytics firm Chainalysis. In 2018, OFAC announced its first crypto-related sanctions against two Iranians.
In the years that followed, these sanctions grew in scale and impact. As seen in the chart below, crypto sanctions are trending upwards over the next few years, with 2022 seeing the largest surge in the number of sanctioned addresses and entities.

OFAC changed its approach when it decided to target cryptocurrency wallets. This graph shows the focus on actions attributed to malicious actors. The report claims law enforcement chose to target “larger organizations” and a variety of services.
The change in approach is due to the large number of cybercriminal activities documented over the past two years. The financial institution targeted hackers, drug dealers, and money laundering activities.
(…) This diversity of entities represents a significant change compared to OFAC’s pre-2021 designations. This was all personal, and at the blockchain level consisted of only a relatively small number of personal wallets.
Chainalysis claims billions of dollars were stolen from digital asset projects and protocols in 2022 alone, but what are the consequences of these new sanctions?
Authorized cryptographic entities are different, should they be handled differently?
Things got complicated at this point, and the impact of sanctions on the cryptocurrency industry has changed as well. In addition to Tornado Cash, the report also looks at darknet marketplace his Hydra and Russian cryptocurrency exchange Garantex.
Each of these entities is different and had different on-chain activities prior to being targeted by OFAC. As you can see in the graph below, the number of funds attributed to ‘legal’ (blue) and ‘illegal’ (orange) varies.
Hydra and Garantex had a steady influx of illicit and “risky” money, but Tornado Cash saw these indicators soar. Decentralized exchanges allow anyone to exchange their tokens, which bad actors use to launder millions of stolen funds.
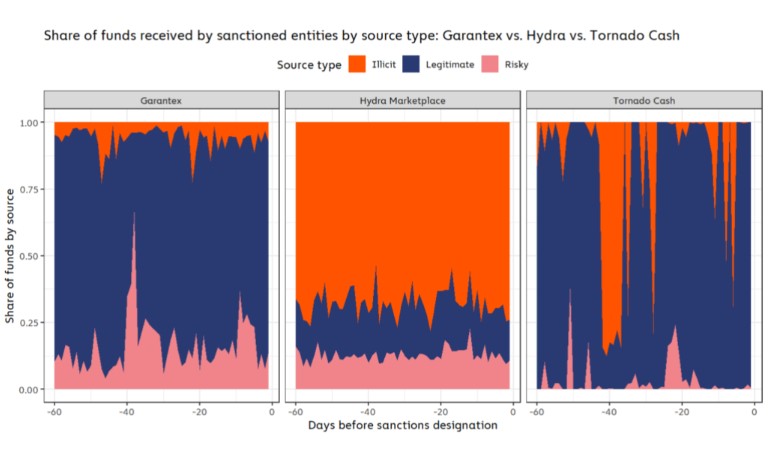
According to data from the report, 34% of funds transferred to Tornado Cash allegedly came from illicit sources, with Hydra and Garantex recording 68% and 6% respectively. However, the decentralized exchange recorded most of these funds in his single transaction by one malicious person.
In that sense, Chainalysis was able to identify the specific illegal activity that underpinned these inflows. While Tornado Cash was mostly funded from hacks and scams, Galantex and Hydra’s funds came from child abuse material, illegal sales, fraud, and more.
After the sanctions, there was 0 inflow from Hydra, a marketplace based in Germany. The country’s authorities cooperated with the sanctions and the platform was dismantled.
Garantex saw the opposite. Bad actors sent more funds to the platform. Under the protection of Russian jurisdiction, no one has attempted to enforce the sanctions imposed by US companies.
Tornado Cash also saw a decline in inflows, but the impact goes beyond this metric. Developers of decentralized exchanges have seen the impact on the real world. One of them he is in law enforcement custody.

Tornado Cash works on a decentralized blockchain using open source software. Its sanctions may have set a dangerous precedent for emerging industries.Moreover, a Chainalysis report shows that sanctions are only effective with support from local institutions.
[ad_2]
Source link

